Example for Using STelnet to Log In to Other Devices (DSA Authentication Mode)
This example shows how to log in to another device by using STelnet. To allow the STelnet client to connect to the SSH server, configure the client and server to generate local key pairs, configure the server to generate a DSA public key, and bind the public key to the client.
Networking Requirements
Large numbers of devices need to be managed and maintained on a network. You cannot connect each device to a terminal. When no reachable route exists between remote devices and a terminal, you can use Telnet to log in to the remote devices from the device that you have logged in to. Telnet provides no secure authentication mode, and data is transmitted in simple mode over TCP, which brings security risks.
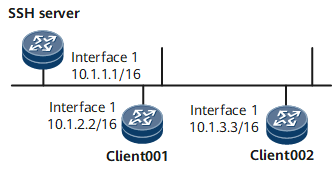
STelnet provides secure Telnet services based on SSH connections. SSH provides encryption and authentication functions to protect devices against attacks, such as IP address spoofing. As shown in Figure 1, after the STelnet server function is enabled on the SSH server, the STelnet client can log in to the SSH server in password, ECC, password-ECC, DSA, password-DSA, RSA, password-RSA, SM2, password-SM2, or all authentication mode.
Precautions
Two users client001 and client002 are configured to log in to the SSH server in the authentication mode of password and DSA respectively.
Configuration Roadmap
The configuration roadmap is as follows:
Configure users client001 and client002 on the SSH server to use different authentication modes to log in to the SSH server.
Configure STelnet client002 and the SSH server to generate local key pairs, and bind the DSA public key of the SSH client to client002 to authenticate the client when the client logs in to the server.
Enable the STelnet server function on the SSH server.
Set the service type of client001 and client002 to STelnet.
Enable first authentication on the SSH client.
Client001 and client002 log in to the SSH server by using STelnet.
Data Preparation
To complete the configuration, you need the following data:
Password authentication for client001
DSA authentication (public key: dsakey001) for client002
IP address of the SSH server: 10.1.1.1
Procedure
- Configure the server to generate a local key pair.
<HUAWEI> system-view [~HUAWEI] sysname SSH Server [*HUAWEI] commit [~SSH Server] dsa local-key-pair create Info: The key name will be: SSH SERVER_Host_DSA Info: The key modulus can be any one of the following : 2048. Info: Key pair generation will take a short while. Info: Generating keys... Info: Succeeded in creating the DSA host keys.
- Create SSH users on the server.

There are several authentication modes for SSH users: password, RSA, password-RSA, DSA, password-DSA, ECC, password-ECC, SM2, password-SM2 and All.
If the authentication mode is password, password-ECC, password-DSA, password-sm2 or password-RSA, configure a local user on the server with the same user name.
If the authentication mode is RSA, password-RSA, DSA, password-DSA, SM2, password-SM2, ECC, password-ECC, or All, save the RSA, DSA, SM2, or ECC public key generated on the SSH client to the server.
# Configure VTY user interfaces.
[~SSH Server] user-interface vty 0 4 [*SSH Server-ui-vty0-4] authentication-mode aaa [*SSH Server-ui-vty0-4] protocol inbound ssh [*SSH Server-ui-vty0-4] user privilege level 3 [*SSH Server-ui-vty0-4] commit [~SSH Server-ui-vty0-4] quit
Create an SSH user named client001.
# Create an SSH user named client001 and configure password authentication for the user.
[~SSH Server] ssh user client001 [*SSH Server] ssh user client001 authentication-type password [*SSH Server] commit
# Set a password for client001.
[~SSH Server] aaa [*SSH Server-aaa] local-user client001 password Please configure the password (8-128) Enter Password: Confirm Password:

The password must meet the following requirements:
The password is entered in man-machine interaction mode. The system does not display the entered password.
A password is a string of 8 to 16 case-sensitive characters and must contain at least two types of the following characters: uppercase letters, lowercase letters, digits, and special characters.
- Special characters exclude question marks (?) and spaces. However, spaces are allowed in the password if the password is enclosed in quotation marks.
- Double quotation marks cannot contain double quotation marks if spaces are used in a password.
- Double quotation marks can contain double quotation marks if no space is used in a password.
For example, the password "Aa123"45"" is valid, but the password "Aa 123"45"" is invalid.
The configured password is displayed in ciphertext in the configuration file.
[*SSH Server-aaa] local-user client001 service-type ssh [*SSH Server-aaa] commit [~SSH Server-aaa] quit
Create an SSH user named client002.
# Create an SSH user named client002 and configure DSA authentication for the user.
[~SSH Server] ssh user client002 [*SSH Server] ssh user client002 authentication-type dsa [*SSH Server] ssh authorization-type default root [*SSH Server] commit
- Configure a DSA public key for the server.
# Configure client002 to generate a local key pair.
<HUAWEI> system-view [~HUAWEI] sysname client002 [*HUAWEI] commit [~client002] dsa local-key-pair create Info: The key name will be: client002_Host_DSA Info: The key modulus can be any one of the following : 2048. Info: Key pair generation will take a short while. Info: Generating keys... Info: Succeeded in creating the DSA host keys. [*client002] commit
# Check the DSA public key generated on the client.
[~client002] display dsa local-key-pair public ======================================================== Time of Key pair created : 2013-05-21 17:18:17 Key name : client002_Host_DSA Key modulus : 1024 Key type : DSA Encryption Key ======================================================== Key code: 3082019F 028180 A49C5EAF 906C80B1 C474CCB0 D47C6965 22DFCF3C 9602BAD8 FCE8F7E3 7A69BE18 8CB7D858 6B50EEBC 54BFB089 61A0DD31 5F7F3080 F0DB47E4 ECDCC10E 7EC18D31 35CD78F7 E002FB6B 4CB59BA5 E2CDB898 43FAD059 98B8EEA8 E7395FC7 CA9D1655 47927368 9914AF09 6CFDC125 6CC8A07F DDDE603B F31C4EA4 0B752AC7 817E877F 0214 CBC5C0BC 2D7B6DFE 15A7F9A3 6F6ED15B 6ECC9F27 028180 6D3202E7 4DCAC5DB 97034305 8D79FDB2 76D5CAA2 C8D00C3D 666F61D4 F2E36445 4027FD04 0D61B2A3 AF3CED6B C36CC68D E8DF35F9 FAF802ED 73BCBD66 C55AE0F6 69530C14 1B33A5A1 CF77D636 75A5EF3B 264AB66E 2A8CFFB1 690E45F8 6FACF1B3 E2A11328 C14BA7F3 CA0D198B 3ED94368 45BA5E89 F1ADB79E F459F826 B9A5CF6D 028180 409C0AE7 1DDDDA8C F3924608 DC32728C D6FA51FB B4933D03 E30780E1 676AA9EE E3A9B677 97DB1D3A 57AF479C 3BDC4096 291B4548 43D88851 DCFEB04D 593F1459 9145FB0B 071CEEE5 5F951E64 CA6C4C16 6192B926 9AD8764E E9F8661C 8EC08D08 BD83BCE3 E054EE39 20207689 433B07A1 1219B9F3 945E88F0 3A8FC0FB 9883905B Host public Key for PEM format Code: ---- BEGIN SSH2 PUBLIC KEY ---- AAAAB3NzaC1kc3MAAACBAKScXq+QbICxxHTMsNR8aWUi3888lgK62Pzo9+N6ab4Y jLfYWGtQ7rxUv7CJYaDdMV9/MIDw20fk7NzBDn7BjTE1zXj34AL7a0y1m6XizbiY Q/rQWZi47qjnOV/Hyp0WVUeSc2iZFK8JbP3BJWzIoH/d3mA78xxOpAt1KseBfod/ AAAAFQDLxcC8LXtt/hWn+aNvbtFbbsyfJwAAAIBtMgLnTcrF25cDQwWNef2ydtXK osjQDD1mb2HU8uNkRUAn/QQNYbKjrzzta8Nsxo3o3zX5+vgC7XO8vWbFWuD2aVMM FBszpaHPd9Y2daXvOyZKtm4qjP+xaQ5F+G+s8bPioRMowUun88oNGYs+2UNoRbpe ifGtt570WfgmuaXPbQAAAIBAnArnHd3ajPOSRgjcMnKM1vpR+7STPQPjB4DhZ2qp 7uOptneX2x06V69HnDvcQJYpG0VIQ9iIUdz+sE1ZPxRZkUX7Cwcc7uVflR5kymxM FmGSuSaa2HZO6fhmHI7AjQi9g7zj4FTuOSAgdolDOwehEhm585ReiPA6j8D7mIOQ Ww== ---- END SSH2 PUBLIC KEY ---- Public key code for pasting into OpenSSH authorized_keys file: ssh-dss AAAAB3NzaC1kc3MAAACBAKScXq+QbICxxHTMsNR8aWUi3888lgK62Pzo9+N6ab4YjLfYWGtQ7rxUv7CJYaDdMV9/MIDw20fk7NzBDn7BjTE1zXj34AL7a0y1m6XizbiYQ/rQWZi47qjnOV/Hyp0WVUeSc2iZFK8JbP3BJWzIoH/d3mA78xxOpAt1KseBfod/AAAAFQDLxcC8LXtt/hWn+aNvbtFbbsyfJwAAAIBtMgLnTcrF25cDQwWNef2ydtXKosjQDD1mb2HU8uNkRUAn/QQNYbKjrzzta8Nsxo3o3zX5+vgC7XO8vWbFWuD2aVMMFBszpaHPd9Y2daXvOyZKtm4qjP+xaQ5F+G+s8bPioRMowUun88oNGYs+2UNoRbpeifGtt570WfgmuaXPbQAAAIBAnArnHd3ajPOSRgjcMnKM1vpR+7STPQPjB4DhZ2qp7uOptneX2x06V69HnDvcQJYpG0VIQ9iIUdz+sE1ZPxRZkUX7Cwcc7uVflR5kymxMFmGSuSaa2HZO6fhmHI7AjQi9g7zj4FTuOSAgdolDOwehEhm585ReiPA6j8D7mIOQWw== dsa-key# Copy the DSA public key generated on the client to the server.
[*SSH Server] dsa peer-public-key dsakey001 encoding-type der Info: Enter "DSA public key" view, return system view with "peer-public-key end". [*SSH Server-dsa-public-key] public-key-code begin Info: Enter "DSA key code" view, return last view with "public-key-code end". [*SSH Server-dsa-public-key-dsa-key-code] 3082019F [*SSH Server-dsa-public-key-dsa-key-code] 028180 [*SSH Server-dsa-public-key-dsa-key-code] A49C5EAF 906C80B1 C474CCB0 D47C6965 22DFCF3C [*SSH Server-dsa-public-key-dsa-key-code] 9602BAD8 FCE8F7E3 7A69BE18 8CB7D858 6B50EEBC [*SSH Server-dsa-public-key-dsa-key-code] 54BFB089 61A0DD31 5F7F3080 F0DB47E4 ECDCC10E [*SSH Server-dsa-public-key-dsa-key-code] 7EC18D31 35CD78F7 E002FB6B 4CB59BA5 E2CDB898 [*SSH Server-dsa-public-key-dsa-key-code] 43FAD059 98B8EEA8 E7395FC7 CA9D1655 47927368 [*SSH Server-dsa-public-key-dsa-key-code] 9914AF09 6CFDC125 6CC8A07F DDDE603B F31C4EA4 [*SSH Server-dsa-public-key-dsa-key-code] 0B752AC7 817E877F [*SSH Server-dsa-public-key-dsa-key-code] 0214 [*SSH Server-dsa-public-key-dsa-key-code] CBC5C0BC 2D7B6DFE 15A7F9A3 6F6ED15B 6ECC9F27 [*SSH Server-dsa-public-key-dsa-key-code] 028180 [*SSH Server-dsa-public-key-dsa-key-code] 6D3202E7 4DCAC5DB 97034305 8D79FDB2 76D5CAA2 [*SSH Server-dsa-public-key-dsa-key-code] C8D00C3D 666F61D4 F2E36445 4027FD04 0D61B2A3 [*SSH Server-dsa-public-key-dsa-key-code] AF3CED6B C36CC68D E8DF35F9 FAF802ED 73BCBD66 [*SSH Server-dsa-public-key-dsa-key-code] C55AE0F6 69530C14 1B33A5A1 CF77D636 75A5EF3B [*SSH Server-dsa-public-key-dsa-key-code] 264AB66E 2A8CFFB1 690E45F8 6FACF1B3 E2A11328 [*SSH Server-dsa-public-key-dsa-key-code] C14BA7F3 CA0D198B 3ED94368 45BA5E89 F1ADB79E [*SSH Server-dsa-public-key-dsa-key-code] F459F826 B9A5CF6D [*SSH Server-dsa-public-key-dsa-key-code] 028180 [*SSH Server-dsa-public-key-dsa-key-code] 409C0AE7 1DDDDA8C F3924608 DC32728C D6FA51FB [*SSH Server-dsa-public-key-dsa-key-code] B4933D03 E30780E1 676AA9EE E3A9B677 97DB1D3A [*SSH Server-dsa-public-key-dsa-key-code] 57AF479C 3BDC4096 291B4548 43D88851 DCFEB04D [*SSH Server-dsa-public-key-dsa-key-code] 593F1459 9145FB0B 071CEEE5 5F951E64 CA6C4C16 [*SSH Server-dsa-public-key-dsa-key-code] 6192B926 9AD8764E E9F8661C 8EC08D08 BD83BCE3 [*SSH Server-dsa-public-key-dsa-key-code] E054EE39 20207689 433B07A1 1219B9F3 945E88F0 [*SSH Server-dsa-public-key-dsa-key-code] 3A8FC0FB 9883905B [*SSH Server-dsa-public-key-dsa-key-code] public-key-code end [*SSH Server-dsa-public-key] peer-public-key end [*SSH Server] commit
- Bind the DSA public key to client002.
[~SSH Server] ssh user client002 assign dsa-key dsakey001 [*SSH Server] commit
- Enable the STelnet server function on the SSH server.
# Enable the STelnet server function.
[~SSH Server] stelnet server enable [*SSH Server] ssh server-source -i GigabitEthernet0/0/0 [*SSH Server] commit
- Set the service type of client001 and client002 to STelnet.
[~SSH Server] ssh user client001 service-type stelnet [*SSH Server] ssh user client002 service-type stelnet [*SSH Server] commit
- Connect STelnet clients to the SSH server.
# If the client logs in to the server for the first time, enable first authentication on the client.
Enable first authentication on client001.
<HUAWEI> system-view [~HUAWEI] sysname client001 [*HUAWEI] commit [~client001] ssh client first-time enable [*client001] commit
Enable first authentication on client002.
[*client002] ssh client first-time enable [*client002] commit
# Log in to the SSH server in password authentication mode on STelnet client001 by entering the username and password.
[~client001] stelnet 10.1.1.1 Please input the username:client001 Trying 10.1.1.1 ... Press CTRL+K to abort Connected to 10.1.1.1 ... The server is not authenticated. Continue to access it?(Y/N):y Save the server's public key?(Y/N):y The server's public key will be saved with the name 10.1.1.1. Please wait... Enter password:The following information indicates that the login is successful:
Info: The max number of VTY users is 20, and the number of current VTY users on line is 6. The current login time is 2011-01-06 11:42:42. <SSH Server># Client002 logs in to the SSH server in DSA authentication mode.
[~client002] stelnet 10.1.1.1 Trying 10.1.1.1 ... Press CTRL + K to abort Connected to 10.1.1.1 ... Please input the username: client002 Please select public key type for user authentication [R for RSA/D for DSA/E for ECC] Please select [R/D/E]: Enter password: Warning: The initial password poses security risks. The password needs to be changed. Change now? [Y/N]:n Info: The max number of VTY users is 15, the number of current VTY users online is 1, and total number of terminal users online is 1. The current login time is 2015-07-13 15:33:08. The last login time is 2015-07-13 15:26:18 from 127.0.0.1 through SSH. <SSH Server>If the login succeeds, the user view is displayed. If the login fails, the message Session is disconnected is displayed.
- Verify the configuration.
# Check the status of the SSH server.
[~SSH Server] display ssh server status SSH Version : 2.0 SSH authentication timeout (Seconds) : 60 SSH authentication retries (Times) : 3 SSH server key generating interval (Hours) : 0 SSH version 1.x compatibility : Enable SSH server keepalive : Disable SFTP IPv4 server : Enable SFTP IPv6 server : Enable STELNET IPv4 server : Enable STELNET IPv6 server : Enable SNETCONF IPv4 server : Enable SNETCONF IPv6 server : Enable SNETCONF IPv4 server port(830) : Disable SNETCONF IPv6 server port(830) : Disable SCP IPv4 server : Enable SCP IPv6 server : Enable SSH IPv4 server port : 22 SSH IPv6 server port : 22 SSH server source address : 10.1.1.1 SSH ipv6 server source address : 0::0 SSH ipv6 server source vpnName : ACL name : ACL number : ACL6 name : ACL6 number : SSH server ip-block : Enable
# Check information about SSH users.
[~SSH Server] display ssh user-information ---------------------------------------------------- User Name : client001 Authentication-Type : password User-public-key-name : - User-public-key-type : - Sftp-directory : - Service-type : stelnet User Name : client002 Authentication-Type : dsa User-public-key-name : dsakey001 User-public-key-type : - Sftp-directory : - Service-type : stelnet ----------------------------------------------------
Configuration Files
SSH server configuration file
# sysname SSH Server # interface GigabitEthernet0/0/0 undo shutdown ip address 10.1.1.1 255.255.0.0 # dsa peer-public-key dsakey001 public-key-code begin 3082019F 028180 A49C5EAF 906C80B1 C474CCB0 D47C6965 22DFCF3C 9602BAD8 FCE8F7E3 7A69BE18 8CB7D858 6B50EEBC 54BFB089 61A0DD31 5F7F3080 F0DB47E4 ECDCC10E 7EC18D31 35CD78F7 E002FB6B 4CB59BA5 E2CDB898 43FAD059 98B8EEA8 E7395FC7 CA9D1655 47927368 9914AF09 6CFDC125 6CC8A07F DDDE603B F31C4EA4 0B752AC7 817E877F 0214 CBC5C0BC 2D7B6DFE 15A7F9A3 6F6ED15B 6ECC9F27 028180 6D3202E7 4DCAC5DB 97034305 8D79FDB2 76D5CAA2 C8D00C3D 666F61D4 F2E36445 4027FD04 0D61B2A3 AF3CED6B C36CC68D E8DF35F9 FAF802ED 73BCBD66 C55AE0F6 69530C14 1B33A5A1 CF77D636 75A5EF3B 264AB66E 2A8CFFB1 690E45F8 6FACF1B3 E2A11328 C14BA7F3 CA0D198B 3ED94368 45BA5E89 F1ADB79E F459F826 B9A5CF6D 028180 409C0AE7 1DDDDA8C F3924608 DC32728C D6FA51FB B4933D03 E30780E1 676AA9EE E3A9B677 97DB1D3A 57AF479C 3BDC4096 291B4548 43D88851 DCFEB04D 593F1459 9145FB0B 071CEEE5 5F951E64 CA6C4C16 6192B926 9AD8764E E9F8661C 8EC08D08 BD83BCE3 E054EE39 20207689 433B07A1 1219B9F3 945E88F0 3A8FC0FB 9883905B public-key-code end peer-public-key end # stelnet server enable ssh server-source -i GigabitEthernet0/0/0 ssh user client001 ssh user client001 authentication-type password ssh user client001 service-type stelnet ssh user client002 ssh user client002 assign dsa-key dsakey001 ssh user client002 authentication-type dsa ssh authorization-type default root ssh user client002 service-type stelnet # aaa local-user client001 password cipher @%@%UyQs4,KTtSwJo(4QmW#K,LC:@%@% local-user client001 service-type ssh # user-interface vty 0 4 authentication-mode aaa protocol inbound ssh user privilege level 3 # return
Client001 configuration file
# sysname client001 # interface GigabitEthernet0/0/0 ip address 10.1.2.2 255.255.255.0 # ssh client first-time enable # returnClient002 configuration file
# sysname client002 # interface GigabitEthernet0/0/0 ip address 10.1.3.3 255.255.255.0 # ssh client first-time enable # return