Service PWs consist of common PWs and bypass PWs. If tunnel protection is available on the public network, you do not need to configure any bypass PW.
Context
On the network shown in Figure 1, PE1 is single-homed to the SPE. To implement MS-PW redundancy:
Configure a dynamic SS-PW between PE1 and the SPE.
Configure dynamic VPWS switching in master/slave mode on the SPE.
Configure a bypass PW between PE2 and PE3.
Figure 1 MS-PW redundancy when a PE is single-homed to an SPE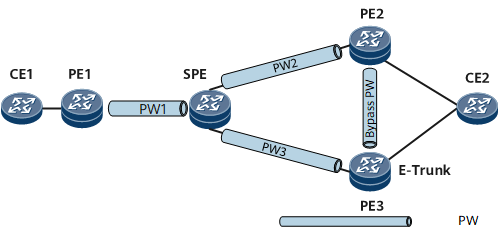
Procedure
- Perform the following configurations on PE1.
- Run the system-view command to enter the system view.
- Run the interface interface-type interface-number command to enter the AC interface view for the service PW.
- Run the mpls l2vc { ip-address | pw-template pw-template-name } * vc-id [ tunnel-policy policy-name [ endpoint endpoint-address color color-value ] | [ control-word | no-control-word ] | [ raw | tagged ] | access-port | ignore-standby-state ] * command to configure PE1 to access the SPE over a dynamic PW.

When creating a PW, you need to specify the IP address and VC ID of the destination PE. The VC IDs at both ends of a VC must be consistent.
According to the default tunnel policy, a dynamic PW uses the LSP as its bearer tunnel, and the load balancing number is 1. To use a different type of tunnel, set the tunnel-policy policy-name parameter for the PW to reference the corresponding tunnel policy. Before referencing a tunnel policy, perform operations described in Configuring a Tunnel Policy and Applying a Tunnel Policy to a VPN.
The encapsulation types at both ends of a PW must be the same.
- Run the commit command to commit the configuration.
- Perform the following configurations on the SPE.
- Run the system-view command to enter the system view.
- Run the mpls switch-l2vc [ instance-name instance-name ] ip-address vc-id [ tunnel-policy policy-name [ endpoint endpoint-address color color-value ] ] between ip-address vc-id [ tunnel-policy policy-name [ endpoint endpoint-address color color-value ] ] [ backup ip-address vc-id [ tunnel-policy policy-name [ endpoint endpoint-address color color-value ] ] encapsulation encapsulation-type [ control-word-transparent ] command to configure dynamic VPWS switching in master/slave mode.
- (Optional) Run the mpls switch-l2vc ip-address pwId encapsulation encapsulation-type reroute { delay delay-time | immediately | never } command to configure a switchback policy for the primary and secondary PWs working in master/slave mode.
- (Optional) Run the mpls switch-l2vc ip-address vc-id encapsulation encapsulation-type switchover command to manually switch service traffic from the primary PW to the secondary PW.
In normal cases, this command is not used. In debugging or fault scenarios, to switch service traffic to the secondary PW temporarily or for a long time, run this command to forcibly perform a primary/secondary PW switchover.
- Run the commit command to commit the configuration.
- Perform the following steps on PE2 and PE3.
- Run the system-view command to enter the system view.
- Run the interface interface-type interface-number command to enter the AC interface view for the service PW.
- Run the mpls l2vc { ip-address | pw-template pw-template-name } * vc-id [ [ control-word | no-control-word ] | [ raw | tagged | ip-interworking | ip-layer2 ] | tunnel-policy policy-name [ endpoint endpoint-address color color-value ] | access-port | [ secondary ] ] * command to configure the primary and secondary PWs.
The primary PW must have the same encapsulation type as the secondary or bypass PW.
The MTUs and control words of the AC interfaces on PE1, PE2, and PE3 must be the same. Otherwise, the PWs may go down, causing traffic interruption.
- Run the mpls l2vc { ip-address | pw-template pw-template-name } * vc-id [ [ control-word | no-control-word ] | [ raw | tagged | ip-interworking | ip-layer2 ] | tunnel-policy policy-name [ endpoint endpoint-address color color-value ] | access-port | bypass ] * command to configure a bypass PW.
The status (enabled or disabled) of the control word function must be the same for the bypass and primary PWs.
- Run the commit command to commit the configuration.

