Configuring Private Network IP FRR
This section describes how to configure private network IP FRR. At a VPN site where multiple CEs connect to the same PE, this feature can immediately switch traffic to another PE-CE link when the next hop of the active route is unreachable.
Usage Scenario
This feature is suitable for IP services that are sensitive to the packet loss and delay on a private network. After private network IP FRR is configured, traffic is immediately switched to another PE-CE link when the next hop of the active route is unreachable. This reduces IP service interruption time.
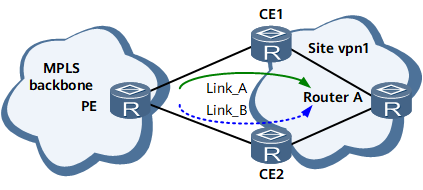
On the network shown in Figure 1, in normal situations, the PE selects Link_A to forward traffic to site vpn1 and uses Link_B as the backup link. If the PE detects that the route to CE1 is unreachable, it will immediately switch traffic to Link_B and private network routes will be converged. Private network IP FRR minimizes the impact on VPN services.
At present, the NetEngine 8000 F supports the following private network IP FRR modes:
IP FRR: applies to the networking where different PE-CE pairs use different routing protocols.
Private network BGP auto FRR: applies to the networking where BGP runs between the PEs and CE.
Pre-configuration Tasks
Before configuring private network IP FRR, complete the following tasks:
Configure a BGP/MPLS IP VPN.
Configure the PE to learn private network routes with the same prefix from different CEs attached to it.
Procedure
- Configure IP FRR.
- Configure private network BGP auto FRR.
- (Optional) Enable IP FRR poison reverse.
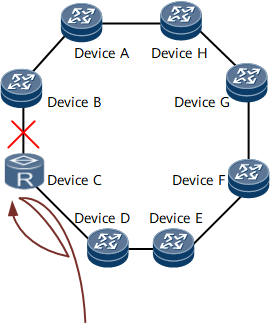
In Figure 2, IP FRR is deployed on the IP ring network, and the traffic enters the ring network from Device D and leaves the ring network from Device A. The primary and secondary next hops of Device D are Device C and Device E, respectively. The primary and secondary next hops of Device C are Device B and Device D, respectively. If the link between Device B and Device C fails and the traffic reaches Device C, Device C forwards the traffic back to Device D. However, before the route convergence is complete, Device D cannot detect the link failure between Device B and Device C, and continues to forward the traffic to Device C. As a result, an instantaneous traffic storm is generated between Device C and Device D. After Device D detects the link failure between Device B and Device C through the route convergence, the traffic is forwarded from Device D to the secondary next hop, Device E.
To prevent instantaneous traffic storms caused by the route convergence and enable Device D to detect the link failure quickly, the poison-reverse enable command can be configured to enable IP FRR poison reverse. Device D forwards the traffic to Device E if the following conditions are met:
The next hop obtained based on the destination IP address in the FIB is the FRR primary interface.
The FRR primary interface is Up.
The outbound interface information is the same as the inbound interface information.
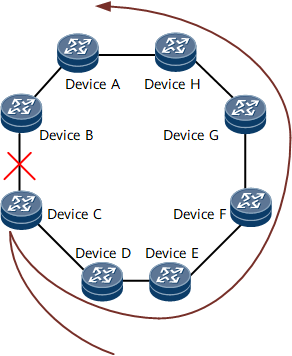
If the link between Device B and Device C fails, the traffic forwarded from Device D to Device C goes back to Device D. However, Device D will not forward the traffic to Device C again but forward it to the secondary next hop, Device E. In Figure 3, the traffic leaves the ring network from Device A.