Man-in-the-middle Attack, IP/MAC Spoofing Attack, and DHCP Exhaustion Attack
This chapter provides an overview of man-in-the-middle attacks, IP or media access control (MAC) spoofing attacks, and Dynamic Host Configuration Protocol (DHCP) exhaustion attacks, and offers solutions to these attacks.
Mechanism
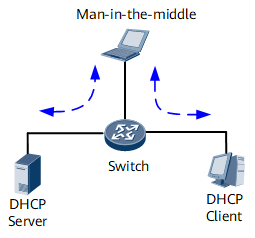
Man-in-the-middle attack
A man-in-the-middle attack is a form of active eavesdropping. The attacker relays packets between a DHCP client and a DHCP server in order to make them believe that they are talking directly to each other over a private connection, when the entire conversation is actually controlled by the attacker.
As shown in Figure 1, the middleman constructs a DHCP packet with its own MAC address and the DHCP server's IP address and sends the packet to the DHCP client. After receiving the packet, the DHCP client learns the middleman's MAC address. As a result, all the packets sent from the DHCP client to the server pass through the middleman. Alternatively, the middleman constructs a DHCP packet with its own MAC address and the DHCP client's IP address and sends the packet to the DHCP server. After receiving the packet, the DHCP server learns the middleman's MAC address. As a result, all the packets sent from the DHCP client to the server pass through the middleman. The DHCP server considers that all packets are sent to or from the DHCP client, and the DHCP client considers that all packets are sent to or from the DHCP server. Packets, however, have been processed on the middleman.
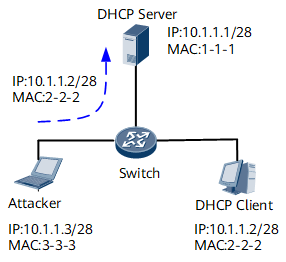
IP/MAC spoofing attack
A spoofing attack is a situation in which one person or program successfully masquerades as another by falsifying data and therefore gaining an illegitimate advantage.
An attacker sends a packet carrying the IP and MAC addresses of an authorized DHCP client to the DHCP server. The DHCP server considers the attacker an authorized DHCP client and learns its IP and MAC addresses. The authorized DHCP client, however, fails to obtain services from the DHCP server, as shown in Figure 2.
DHCP exhaustion attack
A DHCP exhaustion attack is launched by sending bogus DHCP request packets for extending IP address leases. If an attacker simulates authorized clients to continually send DHCP request packets for extending IP address leases, some expired IP addresses cannot be reused.
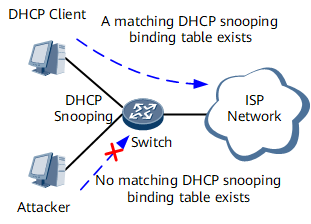
Solution
As shown in Figure 3, a DHCP snooping binding table is used to protect against the preceding attacks. Table 1 lists solutions to the preceding attacks.
Attack Packet |
Association |
Description |
|---|---|---|
Bogus IP packet |
Association between DHCP snooping and IP source guard |
After receiving an IP packet, the device checks whether information carried in the packet (such as the source IP and MAC addresses) matches an entry in the DHCP snooping binding table. If a matching entry exists, the device considers the packet valid and forwards it. If no matching entry exists, the device considers the packet an attack packet and discards it. |
Bogus Address Resolution Protocol (ARP) packet |
Association between DHCP snooping and dynamic ARP inspection (DAI) |
After receiving an ARP packet, the device checks whether information carried in the packet (such as the source IP and MAC addresses) matches an entry in the DHCP snooping binding table. If a matching entry exists, the device considers the packet valid and forwards it. If no matching entry exists, the device considers the packet an attack packet and discards it. |
Bogus DHCP request packet for extending IP lease |
DHCP snooping |
After receiving a DHCP request packet for extending the IP lease, the device checks whether information carried in the packet (such as the source IP and MAC addresses) matches an entry in the DHCP snooping binding table. If a matching entry exists, the device considers the packet valid and forwards it. If no matching entry exists, the device considers the packet an attack packet and discards it. |

The device discards ARP or IP packets sent from DHCP clients that have static IP addresses, because these DHCP clients have no DHCP snooping binding entries. To allow DHCP clients to access the network using static IP addresses and prevent unauthorized clients from accessing the network, configure a static DHCP snooping binding table.
If a client obtains an IP address and gets offline abnormally, the client cannot release its IP address by sending a DHCP release packet. This problem can be solved by associating ARP with DHCP snooping. After ARP is associated with DHCP snooping, if an IP address is unavailable in the ARP table and its DHCP entry expires, the system performs an ARP probe. If the system cannot detect the client for a specified number of attempts, the system deletes the corresponding entry in the DHCP snooping binding table and instructs the DHCP server to release the IP address.