Starvation Attack
Mechanism
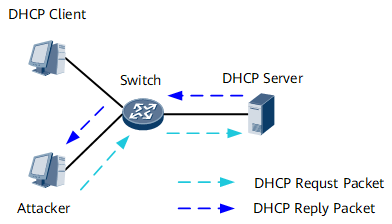
As shown in Figure 1, attackers apply to a Dynamic Host Configuration Protocol (DHCP) server for IP addresses by sending a large number of DHCP packets with varied media access control (MAC) addresses in frame headers. As a result, IP addresses in the address pool are exhausted, and authorized clients cannot obtain IP addresses.
Solution
This attack can be prevented by limiting the number of MAC addresses that an interface can learn.