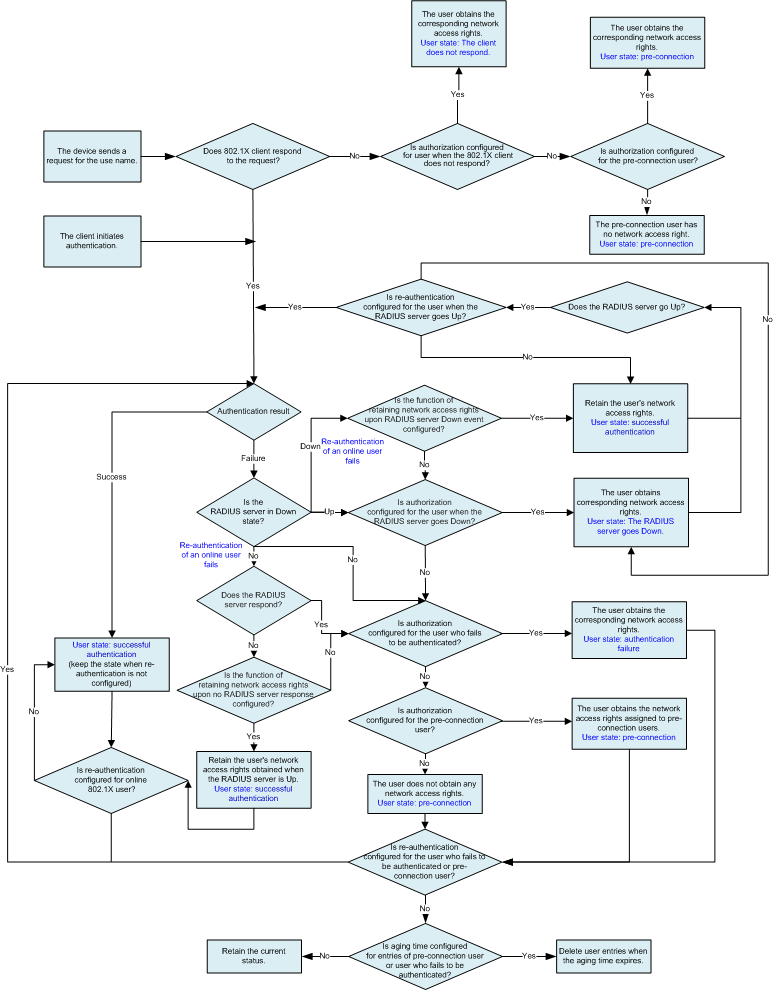
Logical Process of 802.1X Authentication
Figure 1 shows the processing logic of the access device during 802.1X authentication. RADIUS authentication is used as an example.
- When the device sends a request to the client for the user name and the client does not respond, the user obtains the corresponding network access rights if authorization upon no 802.1X client response is configured. If authorization upon no 802.1X client response is not configured, the device checks whether authorization for pre-connection users is configured and authorizes the user accordingly.
- When the client initiates authentication or responds to the authentication request sent from the access device, the user is authenticated successfully and obtains complete access rights if the RADIUS server is in Up state. If the user fails the authentication, the access device checks the authorization configuration upon authentication failures and the authorization configuration for pre-connection users in sequence, and authorizes the user accordingly.
- If the RADIUS server is in Down state, the access device checks the authorization configuration when the authentication server is Down, authorization configuration upon authentication failures, and authorization configuration for pre-connection users in sequence, and authorizes the user accordingly.
- If re-authentication is configured, re-authentication is performed for the user in the corresponding state according to the re-authentication trigger mechanism.
- If re-authentication after a successful authentication fails and the authentication server is in Down state, the access device checks the configuration of retaining the user's network access rights upon the authentication server Down event, the authorization configuration upon the authentication server Down event, the authorization configuration upon authentication failures, and the authorization configuration for pre-connection users in sequence, and authorizes the user accordingly. If the RADIUS server is in Up state but does not respond, the access device checks the configuration of retaining the user's network access rights upon no server response, the authorization configuration upon authentication failures, and the authorization configuration for pre-connection users in sequence, and authorizes the user accordingly.

Wireless 802.1X users only support the authorization configurations of retaining network access rights when the authentication server goes Down and retaining network access rights when the authentication server does not respond.
For details, see the following topics: