Digital Certificate
A digital certificate, or certificate, which is signed by the trusted certificate authority (CA) using digital signature, includes the certificate owner's public key and identity information.
The digital certificate is similar to the passport or identity card. People are requested to show their passports when entering foreign countries. The digital certificate shows the identity of a device or user that requests to access a network.
It ensures that one public key is possessed by only one owner.
Digital Certificate Structure
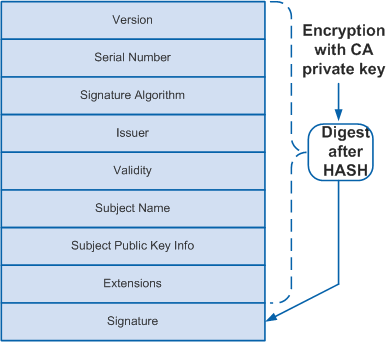
An X.509 v3 digital certificate contains mandatory information such as public key, name, and digital signature of the CA, and optional information such as validity period of the key, issuer (CA) name, and serial number. Figure 1 shows the typical structure of a digital certificate.
Meaning of each field in the digital certificate:
- Version: version of X.509. Generally, the v3 (0x2) is used.
- Serial Number: a positive and unique integer assigned by the issuer to the certificate. Each certificate is uniquely identified by the issuer name and the serial number.
- Signature Algorithm ID: signature algorithm used by the issuer to sign the certificate.
- Issuer: name of the device that has issued a certificate. It must be the same as the subject name in the digital certificate. Generally, the issuer name is the CA server's name.
- Validity: time interval during which a digital certificate is valid, including the start and end dates. The expired certificates are invalid.
- Subject: name of the entity that possesses a digital certificate. In a self-signed certificate, the issuer name is the same as the subject name.
- Subject Public Key Info: public key and the algorithm with which the key is generated.
- Extensions: a sequence of optional fields such as key usage and CRL distributing address.
- Signature: signature signed on a digital certificate by the issuer using the private key.
Digital Certificate Types
There are four types of certificates, as described in Table 1.
| Type | Definition | Description |
|---|---|---|
Self-signed certificate |
A self-signed certificate, which is also called root certificate, is issued by an entity to itself. In this certificate, the issuer name and subject name are the same. |
If an applicant fails to apply for a local certificate from the CA, it can generate a self-signed certificate. The self-signed certificate issuing process is simple. A device does not support lifecycle management (such as certificate update and revocation) over its self-signed certificate. To ensure security of the device and certificate, you are advised to replace the self-signed certificate with the local certificate. |
CA certificate |
CA's own certificate. If a PKI system does not have a hierarchical CA structure, the CA certificate is the self-signed certificate. If a PKI system has a hierarchical CA structure, the top CA is the root CA, which owns a self-signed certificate. |
An applicant trusts a CA by verifying its digital signature. Any applicant can obtain the CA's certificate (including the public key) to verify the local certificate issued by the CA. |
Local certificate |
A certificate issued by a CA to the applicant. |
- |
Local device certificate |
A certificate issued by a device to itself according to the certificate issued by the CA. The issuer name in the certificate is the CA server's name. |
If an applicant fails to apply for a local certificate from the CA, it can generate a local device certificate. The local device certificate issuing process is simple. |
Certificate Formats
Three certificate formats are supported, as described in Table 2.
| Format | Description | Description |
|---|---|---|
PKCS#12 |
Saves certificate files in binary format, including or excluding the private key. The commonly used file name extensions include .P12 and .PFX. |
If the file name extension of a certificate is .CER or .CRT, use the Notepad to open this certificate and check the certificate content to differentiate the certificate format.
|
DER |
Saves certificate files in binary format, excluding the private key. The commonly used file name extensions include .DER, .CER, and .CRT. |
|
PEM |
Saves certificate files in ASCII format, including or excluding the private key. The commonly used file name extensions include .PEM, .CER, and .CRT. |